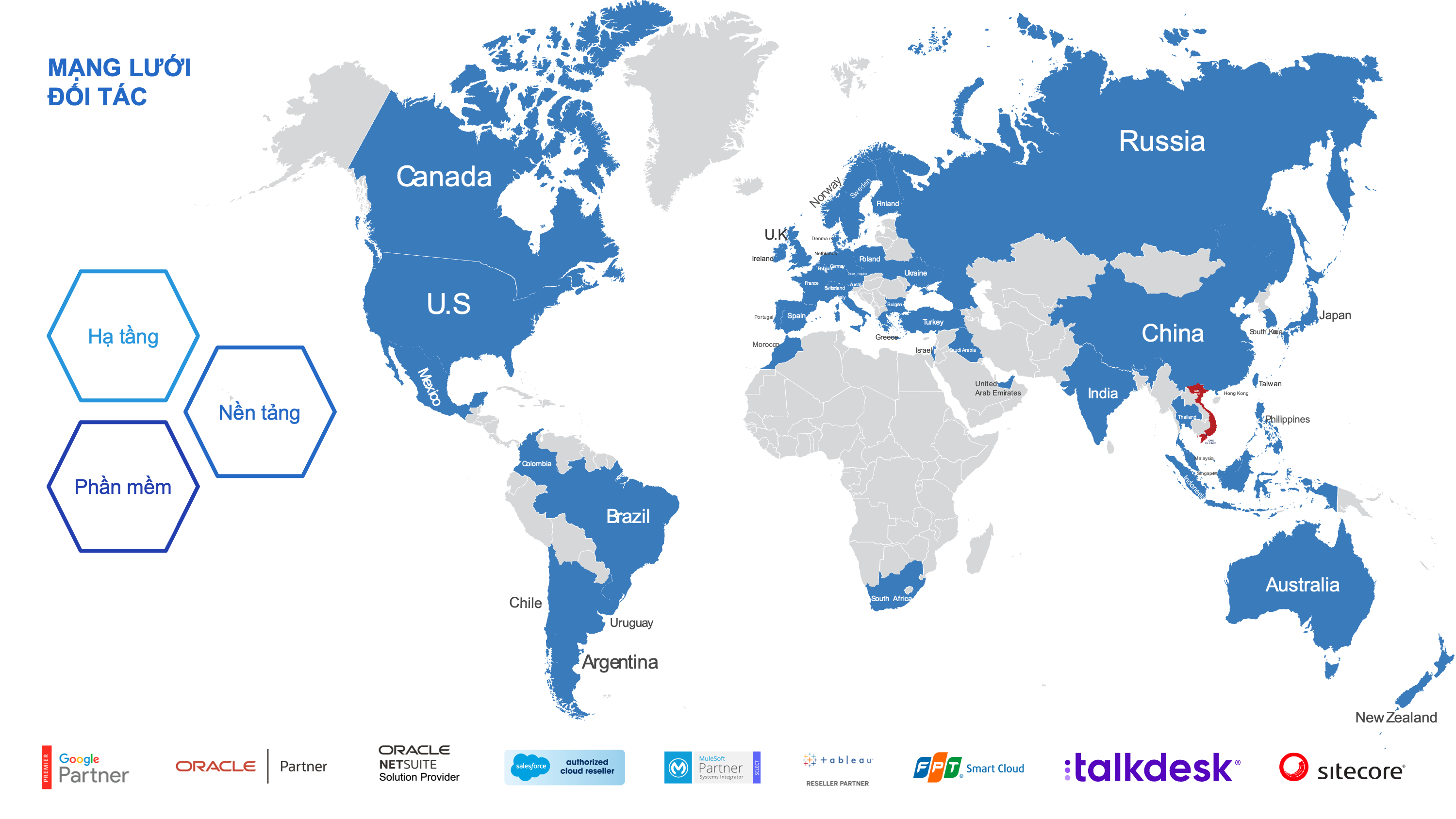
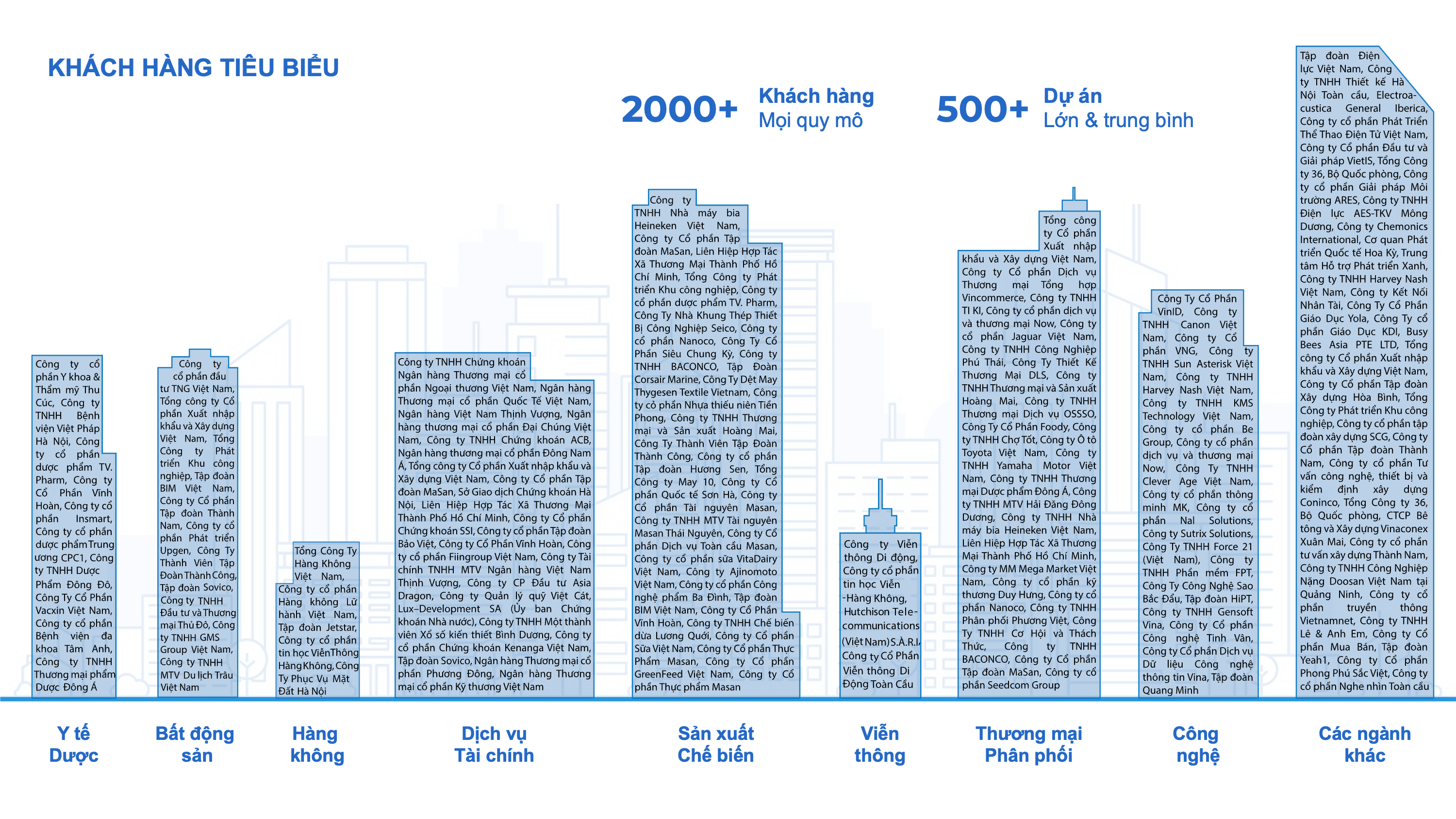
Role-Based Authentication
Home / Role-Based Authentication
Menu
Delighting Security Teams and Users One Login at a Time
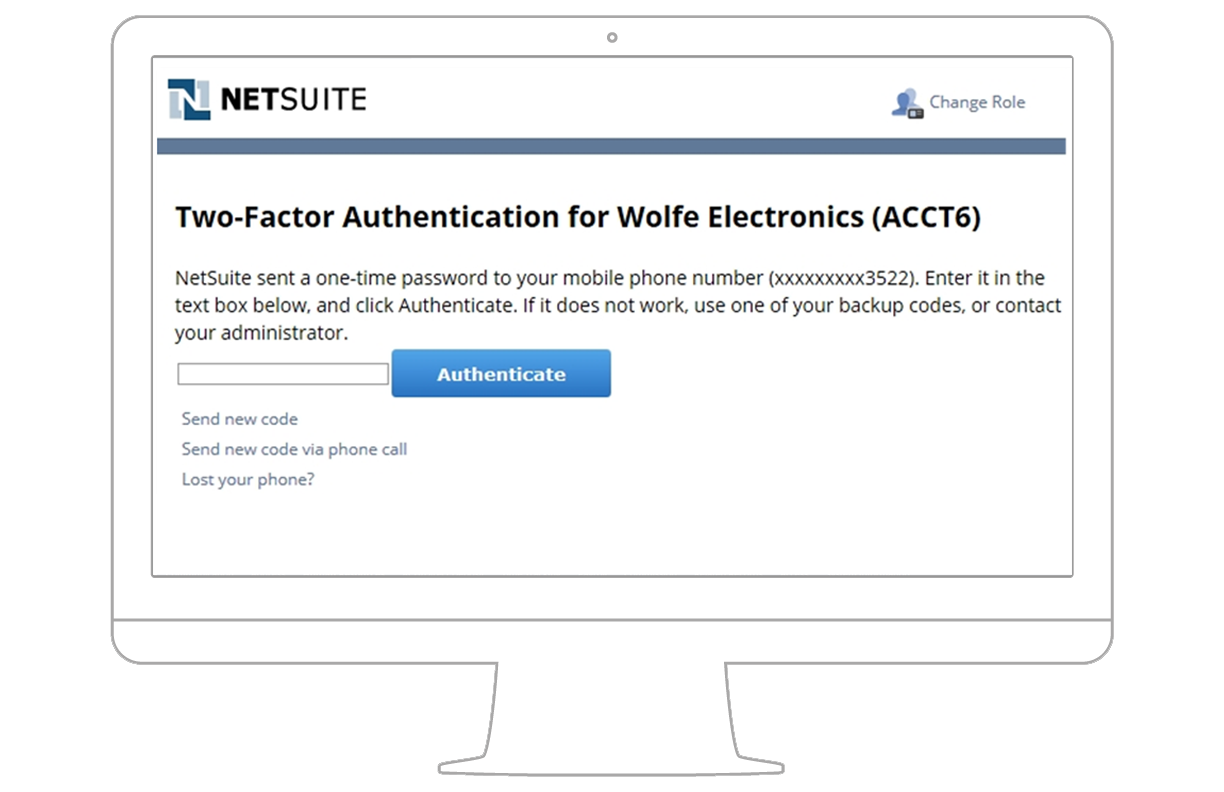
Application users and security organizations agree that NetSuite’s authentication system is remarkable. Admins enjoy the security and benefits of SSAE 16 (SOC1)/ISAE 3402 Type II audited authentication with field-level access administration, while users utilize mobile devices for easy two-factor authentication.
NetSuite provides many standard roles with pre-defined permissions. Most of these roles correspond to common employee positions and standard roles are also available for vendors, partners and customers with account access.
Key Benefits
- Easily manage permissions, access to functionality and access to data for all employees, suppliers and partners using role-based access.
- Confidently access NetSuite from anywhere through 128-bit SSL encryption.
- Utilize advanced security technology such as location-based IP address restrictions.
- Continuously enforce access to NetSuite with password complexity and password renewal rules.